How to Remove Vista Internet Security 2010 Rogue Anti-Spyware?
# This article How to Remove Vista Internet Security 2010 Virus is an article in Spyware Removal Instructions, the original author is Security-Wire.com .You can read more information in the following:
Vista Internet Security 2010 Information:
Vista Internet Security 2010 (can be also called as Vista Internet Security) is a rogue anti-spyware program that changes its name according to the OS of the infected computers. Vista Internet Security 2010 is from the same family as XP Internet Security 2010 and Win 7 Internet Security 2010. Vista Internet Security 2010 is rapidly spreading thru infected facebook/myspace ads or by downloading useless shareware or fake codecs on malicious websites. Once installed, Vista Internet Security 2010 simulates a system scan and reports false scan, displays fake security alerts or notifications and then informs you that you need to pay money to register the program if you want to remove the infections and computer threats. Of course, that’s not true. Vista Internet Security 2010 is a useless program and will not remove any malware from your system. Just ignore what Vista Internet Security 2010 says and remove it with the removal instructions below carefully.
Vista Internet Security 2010 Screenshot:
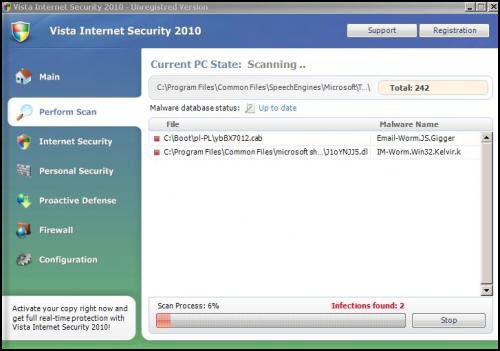
Manual Removal
Note: If you are not proficient with computer, it’s suggested that you backup your registry before manually removing Vista Internet Security 2010 Rogue Anti-Spyware. And double check the entries that you are going to delete, or your computer can’t work for missing some files.
Step 1: End its process by opening Task Manager.
av.exe
Step 2: The registry entries you need to delete:
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “%1″ %*
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “%1″ %*
HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “%1″ %*
HKEY_CLASSES_ROOT\secfile\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “%1″ %*
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = “%UserProfile%\Local Settings\Application Data\av.exe” /START “C:\Program Files\Internet Explorer\iexplore.exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center “AntiVirusOverride” = “1”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center “FirewallOverride” = “1”
Step 3: The files you need to delete:
%UserProfile%\\AppData\\Local\\av.exe
%UserProfile%\\AppData\\Local\\WRblt8464P
Please, be aware that manual removal of Vista Internet Security 2010 Rogue Anti-Spyware is a cumbersome task and can not always ensure complete removal of the malware, due to the fact that some files might be hidden or may get reanimated automatically afterwards. Moreover, manual interference of this kind may cause damage to the system. That’s why it’s strongly recommended automatic removal of Vista Internet Security 2010 Rogue Anti-Spyware, which will save your time and enable avoiding any system malfunctions and guarantee the needed result.
Automatic Vista Internet Security 2010 Rogue Anti-Spyware Removal:
1. Restart your computer and keep pressing F8 Key before Windows launches. Use the arrow keys to select the “Safe Mode with Networking” option, and then hit ENTER Key to continue.
2. Download Vista Internet Security 2010 Virus Remover, install it and update its database to the latest. After that, restart your computer so as to make Vista Internet Security 2010 Virus Remover fully functional. Repeat Step 1 into Safe Mode and run an Online Scan of your computer so that Vista Internet Security 2010 Virus Remover can detect all potential malware in your system.
NOTE: If you have problem installing Vista Internet Security 2010 Virus Remover, you can download this correction script, unzip it and then double click to run it. It will correct your registry settings that the virus has modified. Then double click the program and finish the installation.
3. After the Online Scan finishes, click “Details” for the malware detected to make sure that your important data are not infected and removed. Ignore or select the scan result and click “Remove” to remove the threats. Reboot your computer and let Vista Internet Security 2010 Virus Remover delete all detected virus.
4. Click to repair your corrupted registry
Why should you need to repair the registry?
As we all know, virus and Trojans modify and destroy system registry and make the computer malfunction so that the computer will not perform normally. Even if the virus and Trojans are removed, the registry is still destroyed or modified, so the computer still has problems. That’s the very reason why you need to repair the registry. At the meanwhile, some virus and Trojans leave some DLL files in the registry and this will cause strange DLL errors and affect the computer performance.
To make your computer run as perfectly as before or much faster than before:
1. Download and install Multi-Awarded Registry Tool.
2. Run a full scan of your registry.
3. Click “Repair Problems” and repair all errors detected.
After these 3 easy steps, your computer will run much faster than before within minutes!


Related posts:
Step by Step Remove Win 7 Internet Security 2010 Guide | Spyware Removal Guides on May 13th, 2010
[…] depends on the Operating System it invades. Just like its relatives XP Internet Security 2010 and Vista Internet Security 2010, Win 7 Internet Security 2010 uses scare tactics with an aim to con the user into purchasing its […]